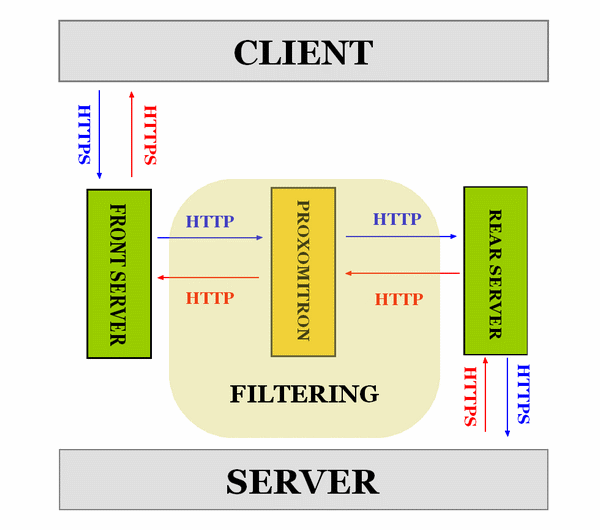
工作原理
安装
- 解压缩 ProxHTTPSProxyMII,并将其中的根证书 "CA.crt" 安装到浏览器的可信任证书区域。
下载
http://proxfilter.net/proxhttpsproxy/Pr ... oxyMII.zip
配置
ProxHTTPSProxyMII 默认监听 8079 端口,并转发 HTTPS 请求到 Proxomitron 默认监听端口 8080。
可编辑 "Config.ini" 文件修改默认监听端口。
更新历史
Code: Select all
Version 1.3.1 (20151001)
--------------
* Certifications are now signed via SHA256 instead of SHA1
Version 1.3 (20150114)
--------------
+ Each request has a number ranged from 001 to 999 for reference. 000 is reserved for SSL requests not MITMed like those in [BLACKLIST] and [SSL Pass-Thru] sections.
+ Log window now displays the length of the bytes submitted in POST method
Version 1.2 (20141221)
--------------
+ Content is streamed to client, while not cached before sending
* Fix config auto reload
* Less exception traceback dumped
* Tagged header changed from "Tagged:Proxomitron FrontProxy/*" to "Tagged:ProxHTTPSProxyMII FrontProxy/*"
Version 1.1 (20141024)
--------------
+ Support URL bypass
+ Handle both HTTP and HTTPS
+ Auto reload config upon chagnes
Version 1.0 (20140729)
--------------
Initial release
Code: Select all
To use
----
* Add the ProxHTTPSProxy rear server to the Proxomitron's list of external proxies
`127.0.0.1:8081 ProxHTTPSProxyMII`
* Add to Proxomitron's "Bypass URLs that match this expression" field if it is empty
`$OHDR(Tagged:ProxHTTPSProxyMII FrontProxy/*)$SETPROXY(127.0.0.1:8081)(^)`
* Add to the beginning of the entry in Proxomitron's "Bypass URLs that match this expression" field if it is **not** empty
`$OHDR(Tagged:ProxHTTPSProxyMII FrontProxy/*)$SETPROXY(127.0.0.1:8081)(^)|`
Tips
----
* Proxomitron always executes some commands in "Bypass URLs that match this expression" field. Adding the entry there allows the Proxomitron to use the rear server when in Bypass mode.
This undocumented feature brings many possibilities but remember, an actual match triggers bypass of filtering!
- `$OHDR(Tagged:ProxHTTPSProxyMII FrontProxy/*)` checks for the header that indicates an https request.
- `$SETPROXY(127.0.0.1:8081)` is executed when found.
- `(^)` expression never matches.
* Identify https connections by testing for the "Tagged" request header that the ProxHTTPSProxy front server adds to the request.
`$OHDR(Tagged:ProxHTTPSProxyMII FrontProxy/*)`
* For local file requests, use an expression like
`$USEPROXY(false)$RDIR(http://local.ptron/killed.gif)`
* Before redirecting "Tagged" connections to external resources consider removing the "Tagged" header.
* If needed, the Proxomitron can still do https. After adding the ssl files to the Proxomitron, use a header filter like
```
[HTTP headers]
In = FALSE
Out = TRUE
Key = "Tagged: Use Proxomitron for https://badcert.com"
URL = "badcert.com$OHDR(Tagged:ProxHTTPSProxyMII FrontProxy/*)$USEPROXY(false)$RDIR(https://badcert.com)"
```
This filter also removes the "Tagged" header.
For the current sidki set
----
1. Add the following two lines to Exceptions-U
```
$OHDR(Tagged:ProxHTTPSProxyMII FrontProxy/*)$SET(keyword=$GET(keyword)i_proxy:3.)(^)
~(^$TST(keyword=i_proxy:[03].))$OHDR(Tagged:ProxHTTPSProxyMII FrontProxy/*)$SET(keyword=$GET(keyword)i_proxy:3.)(^)
```
2. Redirect connections to http resources with an expression like
`$USEPROXY(false)$SET(keyword=i_proxy:0.)$RDIR(http://local.ptron/killed.gif)`